
Signing Office Macros and PowerShell Scripts Part 1
Signing Code and Setting Policy The last few years have shown that ransomware and banking trojans like Emotet and Co. like to spread via scripts
Browse through exciting articles, current news and helpful tips & tricks from our experts on all aspects of cybersecurity.

Signing Code and Setting Policy The last few years have shown that ransomware and banking trojans like Emotet and Co. like to spread via scripts
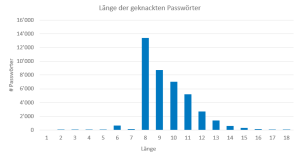
by Sandro Affentranger This is the second article on passwords. Recommendations for strong passwords have hardly changed over the years. Only recently it has become
by Jakob Kunzmann This article deals with the OWASP Top 10 on the Internet of Things, a list of the top ten security risks in

by Sandro Affentranger This is the first instalment in a two-part series about passwords. Passwords have become indispensable these days. For a long time the

by Jakob Kunzmann This is the first of two articles presenting the OWASP Top 10 on the Internet of Things, a list of the top
Penetration testing projects are all about the defined scope and objective, i.e. which systems, entry points, personal or company sites may be attacked, and what

Malware has become a common word understood by the average person. Whether it’s in the media, through fellow users, or because one’s own anti-virus software

The Open Web Application Security Projekt – better known as OWASP, is a manufacturer independent non-profit-Organization with the aim of making (web) applications more secure.

by Marco Wohler The danger from domain administrator accounts is often underestimated. This article describes how attackers can compromise an entire domain. In general, authorizations

by Frank Ully This is the sixth and final instalment in a multi-part series about Windows PowerShell and how attackers abuse it, how incident responders
Never miss the latest news about cybersecurity topics again? Subscribe to our Newsletter.
Subscribe to our news feed on LinkedIn and register to receive our newsletter.
Don’t miss anything! Subscribe to our free newsletter.
Availability Monday to Friday 8:00 a.m. – 6:00 p.m (exception: customers with SLA – please call the 24/7 IRR emergency number).
Private individuals please contact your trusted IT service provider or the local police station.
For more information about our DFIR services here:
