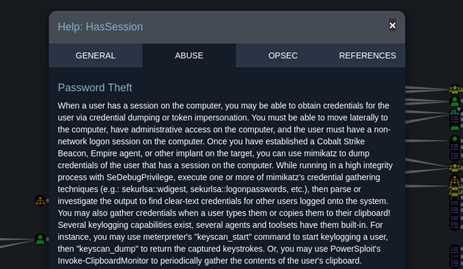
A modern Active Directory environment consists of many different components. There are clients, servers, databases, users, applications and much more. It is easy to lose track of everything (especially as a Red Team). The BloodHound tool can help here.
What Is “BloodHound”?
As the name suggests, BloodHound searches within the Active Directory environment, identifies users and uncovers relationships between the various components.
BloodHound then displays the results in a graph database so that the user can see at a glance what they are dealing with. Moreover, BloodHound can provide additional information about various components, such as group affiliations, lateral movement assistance or hints on how to fix a vulnerability. Another useful feature is the display of the shortest path between two targets.
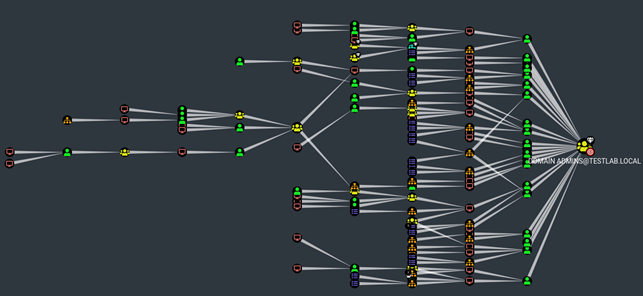
How Does “BloodHound” Work?
Technically, an application called SharpHound is run on an already compromised host, which collects the required information in the Active Directory environment and stores it in files. BloodHound itself uses these files as input data and imports them into a Neo4J graph database.
The tool provides some predefined queries, which help to quickly find your way through. However, it is also possible to write your own (sometimes very complex) queries in order to get precise results.
Furthermore, it is possible to mark individual components as compromised or as a so-called high value target, for example.
BloodHound is also able to provide the user with useful information about the connections between the data points. This includes general information about the relationships of the component as well as possible attack vectors.
Where Is “BloodHound” Used?
The tool is not only used for red teaming, but network administrators can also use BloodHound to find and fix vulnerabilities in their Active Directory environment.
Conclusion
In summary, it is worth noting that the tool is indispensable for any red team operation. Information can be gathered quickly and the “attacker” always knows where they are in the network and can carefully plan their next steps.
If you need advice or support in securing your Active Directory environment, please do not hesitate to contact the Oneconsult team.
About the Author
Philipp Löw graduated with a BSc. BIT degree in Business Information Systems from the Munich University of Applied Sciences in February 2021. Since March 2021, he has been enrolled in the master’s program in IT security, also at the Munich University of Applied Sciences. During his bachelor studies, Philipp Löw worked for a Munich-based software service provider and in research, where he focused on the detection of Indicators of Compromise. Since October 2021, Philipp Löw has been employed as a working student at Oneconsult Deutschland AG.