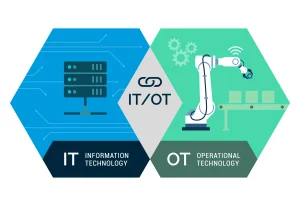
Distinction between Operational Technology and Information Technology
What would you expect power plants, production facilities and transportation companies to have in common? They all use Operational Technology (OT) in sometimes highly critical
Browse through exciting articles, current news and helpful tips & tricks from our experts on all aspects of cybersecurity.

What would you expect power plants, production facilities and transportation companies to have in common? They all use Operational Technology (OT) in sometimes highly critical

In the ever-growing digital era, the security of company data is of paramount importance. Choosing the right password manager plays a crucial role.

In an increasingly digital world where the security of corporate data is a top priority, every organization faces the challenge of protecting sensitive information from

In the digital world, we are exposed to various threats every day. One of the most sophisticated and effective attacks is spear phishing. Unlike regular

Purple teaming results from the merging of the red (team) and the blue (team) and illustrates how the two teams work together to improve the

The Internet of Things (IoT) is omnipresent, connecting more and more physical devices with the digital world. Nevertheless, the topic of IT security is neglected

The vast majority of companies nowadays use Windows and therefore Active Directory. The default settings are often designed for functionality rather than security. Also, when

So-called DDoS attacks (Distributed Denial of Service) on IT infrastructures are on the rise – even authorities and critical infrastructures are affected. Can the SCION

SQL injections are a widespread type of vulnerability in websites, which have high damaging potential. This article is exactly about this type of injections and

Continous Integration (CI) and Continous Deployment (CD) have become important components of software engineering in recent years. Automation enables development teams to deploy new features
Never miss the latest news about cybersecurity topics again? Subscribe to our Newsletter.
Subscribe to our news feed on LinkedIn and register to receive our newsletter.
Don’t miss anything! Subscribe to our free newsletter.
Availability Monday to Friday 8:00 a.m. – 6:00 p.m (exception: customers with SLA – please call the 24/7 IRR emergency number).
Private individuals please contact your trusted IT service provider or the local police station.
For more information about our DFIR services here:
