Purple teaming refers to the close cooperation between attacking (red team) and defending (blue team) security forces. Instead of acting independently, they jointly develop targeted attack scenarios, carry them out together, and analyze the results in direct exchange. This collaborative approach not only allows for vulnerabilities to be uncovered more efficiently but also addresses them directly with appropriate defensive measures.
In this article, you will learn everything you need to know about purple teaming:
- What exactly is purple teaming?
- Which areas of application are particularly suitable?
- How does a purple teaming project typically look like?
- What advantages does purple teaming offer compared to other forms of testing?
- Why has purple teaming established itself as an effective means of improving cybersecurity?
Table of contents
What is Purple Teaming?
In cybersecurity, the teams involved are traditionally divided into two roles during attack simulation: red team and blue team. The blue team is responsible for the defense, for example in the form of an internal security team or a Security Operation Center (SOC). The red team, on the other hand, acts as an attacker, for example through penetration testers.
In most security analyses, these teams work separated from each other. Purple teaming, on the contrary, combines them: red team and blue team collaborate in order to plan, execute, and evaluate attack scenarios together – with the aim of improving security measures in a targeted and efficient manner.
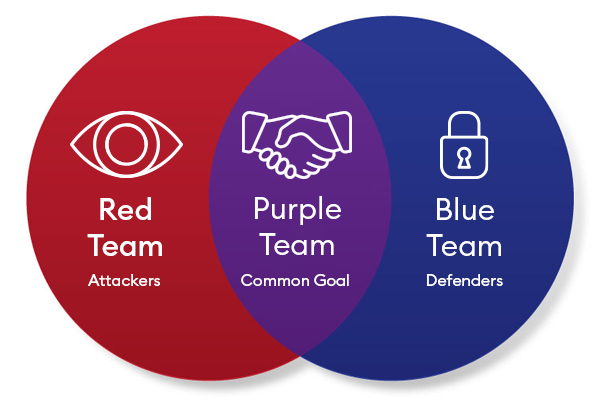
Red Team – The Attackers
The red team takes on the role of a real attacker. It simulates targeted cyberattacks on systems and applications in order to uncover security gaps and circumvent defensive measures. The insights gained are documented and serve as a basis for concrete improvements.
Would you like to learn more about red teaming? In this blog post we take a closer look at this topic.
Blue Team – The Defenders Within the Company
The blue team is responsible for the defense. This can be an internal security team, an external SOC, or even a hybrid approach in which, for example, the first-level analysis is performed by an external SOC and the response is then handled by an internal team.
The blue team detects, analyzes, and reacts to attempted attacks. By using the red team’s information, it can refine its detection mechanisms and eliminate vulnerabilities in a targeted manner.
Purple Team – Collaboration for Improved Cybersecurity
In purple teaming, red team and blue team work hand in hand. During the simulation of attacks, they exchange information in real time: Which attacks were successful? Which attacks were blocked or detected? Is there any room for improvement?
This form of collaboration makes it possible to immediately question and adapt defense strategies. The result is an iterative learning process that goes beyond traditional red teaming approaches and strengthens cyber resilience in the long term. But which specific attack scenarios can actually be tested with purple teaming?
Which Attack Scenarios Can be Tested With Purple Teaming?
Purple teaming is particularly suitable for running through specific attack scenarios and evaluating the effect of existing security measures. The advantage: The tests are realistic but are carried out in a controlled manner, allowing to take a targeted look at individual vulnerabilities.
Below are three typical areas of application for purple teaming projects:
Validation and Optimization of Use Cases & Playbooks
A core value of purple teaming is the targeted testing and improvement of existing use cases, detection rules, or incident response playbooks.
The following can be carried out:
- Testing specific tools or parts of an attack path
- Determining the usefulness of selected use cases
- Identification of inadequacies in blocking or alerting in the event of corresponding attacks
- Questioning the effectiveness of the selected use cases and attempts to circumvent detection
Attack Simulation Based on Real Threat Scenarios
Purple teaming can also be used to simulate realistic attack scenarios, for example based on TTPs (Tactics, Techniques, Procedures) of known attacker groups or past incidents in this sector.
This enables the following, among other things:
- Creating an attack simulation based on known attackers or attack paths
- Identification of gaps during investigation of the entire attack chain
- Search for alternative paths to bypass defense functions
Re-Testing After Incidents or Red Teaming Operations
Preceding safety incidents or classical red teaming exercises, purple teaming is a structured way of checking the effectiveness of improvement measures.
Objectives of such a re-test:
- Recreation of an attack path as observed during an incident or red teaming operation
- Identification of progress compared to previous iterations/tests
- Identification of further potential for improvement
How does a Purple Teaming Project Look Like?
Successful purple teaming relies on clear communication and close collaboration. To gain maximum insights, careful planning is just as crucial as the active cooperation of both teams during the project.
Planning and Preparation
Since purple teaming involves the red team and the blue team working together, coordinated planning is required in advance. Both teams must have a clear understanding of the objective being pursued – for example, the simulation of a specific attacker or the targeted testing of internal use cases.
The preparation effort varies depending on the scenario. For example, if a specific attack path is to be simulated or a specific use case tested, additional information must be obtained and the details clarified in advance. A structured preparation helps to identify potential issues at an early stage and to solve them efficiently during the test.
It is also important that at least one member of the blue team is available for technical queries about the environment, as the scenarios are often based on a mixture of real threat actors, internally defined use cases, and findings from previous red teaming assignments.
Implementation and Technical Cooperation
During implementation, the particular strength of purple teaming comes into effect: direct collaboration. Red team and blue team are in close contact so that they can coordinate in real time or as required. This allows attacks and defensive measures to be coordinated without any delay.
The blue team analyzes the output of its security tools during the simulated attacks and is able to react directly to them, for example by adapting rules, optimizing alerting mechanisms, or testing new detection measures. At the same time, the red team can adapt its attack methods in order to test workarounds.
Follow-up and Lessons Learned
In contrast to classical red teaming projects, purple teaming is not about successfully compromising the environment, but about testing the effectiveness of the security measures together and as efficiently as possible.
Once the tests have been completed, the results will be evaluated together:
- What could be identified?
- What could be blocked?
- Which attacks were successful?
- Is there any room for improvement?
The insights gained serve as the basis for specific measures, such as optimizing detection rules, strengthening internal processes, or further developing existing use cases. This not only leads to better defense strategies but also to a sustainable transfer of know-how between attacker and defender team.
What Makes Purple Teaming Particularly Effective?
Efficiency Through Targeted Collaboration
Purple teaming makes the test process more efficient on both sides. The direct exchange between red team and blue team eliminates the lengthy reconnaissance phase of classical red teaming missions. The attacking side knows which parts of the environment are to be tested and can target specific attack paths or payloads.
At the same time, real-time communication enables the blue team to directly track which attacks were carried out and when, and which of them were detected or not. The insights gained with the security tools can be used immediately to adjust alerting rules, identify gaps, or improve detection.
This close collaboration does not only save time, but also enables focused, resource-saving tests with immediate added value.
Deeper Understanding Through Continuous Feedback
In contrast to classical red teaming projects, where the results are usually only documented and handed over at the end, purple teaming thrives on constant exchange. The teams work together to analyze why an attack was detected or overlooked, discuss alerts, and optimize their strategies while the test is still running.
These iterations provide deeper insights into the actual effectiveness of security measures. In addition, attacks can be carried out again, for example to directly validate an adjustment to the defense or to specifically test new evasion methods. This results in measurable, traceable improvements that are based on real scenarios and go beyond pure theory.
Flexible Adaptation to Real Threats
Purple teaming makes it possible to react dynamically to new insights. If planned scenarios are successfully identified early on in the test, the remaining time can be used to test other use cases, new attack patterns, or targeted evasion techniques.
Conversely, in the event of non-detection, new defense rules can be introduced and immediately tested for their effectiveness. This flexibility makes purple teaming a particularly effective tool for continuously developing defense mechanisms – even beyond the actual test period.
Conclusion – Purple Teaming for More Effective Cybersecurity
Purple teaming is an effective tool for testing defense capabilities in a targeted manner using realistic attack scenarios. In addition, purple teaming allows a broad spectrum of tests, ranging from the complete simulation of an attack path to the focused testing of individual use cases – depending on the objectives and maturity level of the security organization.
Although purple teaming does not replace classical red teaming, it is a valuable addition, for example for validating new measures after a red teaming deployment or for the continuous optimization of existing detection functions. Companies benefit from an efficient, practical testing approach with a high degree of flexibility and direct added value for the defense.
With many years of experience in red and purple teaming projects, Oneconsult helps companies strengthen their cyber resilience in a targeted manner. Our experts support you in running through practical attack scenarios, identifying vulnerabilities, and optimizing your defense measures effectively.