Password spraying and credential stuffing are among the most common methods used by attackers to gain unauthorized access to company systems. Compared to classical brute-force attacks, password spraying attacks are more difficult to detect. They deliberately exploit the human weakness for easy-to-remember passwords. In this article, we explain how these attacks work, what risks they pose, and what measures companies can take to protect themselves effectively.
Table of Contents
- What is Password Spraying?
- The Cybercriminals’ Approach to Password Spraying
- Typical Targets and Vectors of Password Spraying Attacks
- The Difference Between Password Spraying and Credential Stuffing
- How to Prevent Password Spraying and Credential Stuffing?
- Conclusion: Strengthening Cybersecurity Through Awareness and Testing
What is Password Spraying?
Password spraying is an attack technique in which cybercriminals attempt to gain access to a large number of user accounts with a few frequently used passwords. According to the MITRE ATT&CK framework, this attack with the identifier T1110.003 is classified as a specific form of brute-force attack and exploits the fact that many users choose easy-to-guess passwords.
The Cybercriminals’ Approach to Password Spraying
In contrast to classic brute-force attacks, in which attackers try out thousands or even millions of passwords for a single user account, the opposite approach is used during password spraying attacks. This involves trying to log in to a service with a single or a few selected passwords for a list of valid user accounts.
To carry out such an attack, attackers need two components:
- an (insecure) password that is likely to be used by multiple users
- a list of valid user accounts
Below, we explain how cybercriminals obtain these components and how they proceed in detail. We also highlight the measures companies can take to better protect their systems.
Insecure Passwords – How Attackers Deliberately Exploit Them
It is quite easy for attackers to identify insecure passwords. There are numerous collections of leaked passwords that are publicly available, such as the well-known password collections from Kaonashi or ignis-sec (https://github.com/kaonashi-passwords/Kaonashi and https://github.com/ignis-sec/Pwdb-Public).
Downloading the Breaches collection from Have I Been Pwned, which contains several hundred million passwords, or the HashMob lists also provides an overview of which passwords are particularly popular.
However, custom passwords can ultimately be successful as well. Cybercriminals often try to combine the company name with the current year in order to generate passwords that may be used by employees. In the case of Oneconsult, that could be, for example, Oneconsult2025!.
User Enumeration – How Attackers Identify Valid Accounts
The enumeration of valid user names in a company can be somewhat more difficult for attackers. A distinction should be made as to whether the attack comes from outside the company (e.g., on a web portal) or from within the company (e.g., against domain users).
From an external attack perspective, there are various ways of identifying valid users. For example, web portals themselves can provide information about whether a user account exists or not through error messages.
Figure 1 exemplarily shows how valid users can be identified by means of error messages. After entering a few different user names, attackers can recognize the following pattern: If the user exists, the error message «Wrong Password!» is displayed. If the user does not exist, the server returns «Wrong Username!».
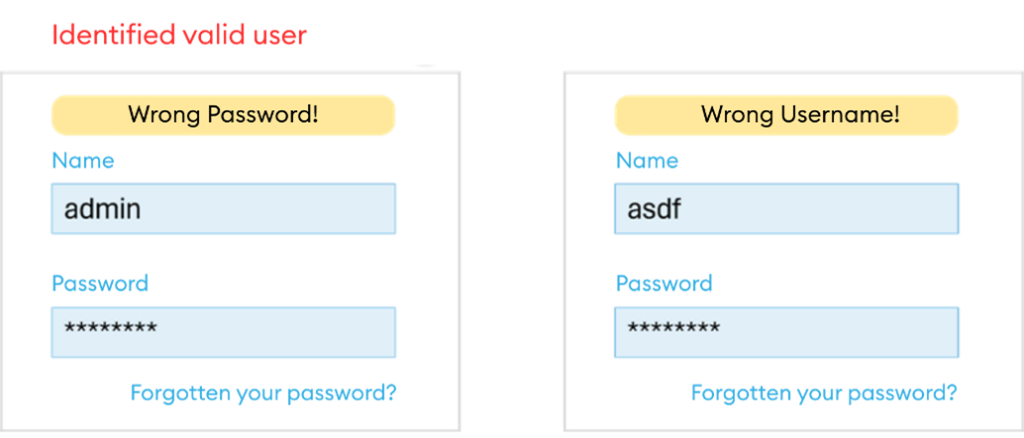
Figure 1: Identification of valid users
Attackers can also try to enumerate valid users via cloud endpoints. For Microsoft 365, the o365creeper tool is useful for this purpose. This Python script uses a list of potentially valid usernames and sends them against the Microsoft endpoint /common/GetCredentialType. Depending on whether the user name exists or not, the parameter IfExistsResult returns 0 or 1 in the server’s response.
A typical request could look like this:
o365creeper.py -f potenzielle-benutzernamen.txt -o valide-benutzernamen.txtOf course, attackers can also resort to breach lists, as they do when searching for weak passwords. In addition to Have I Been Pwned or various platforms where data leaks are published or offered for sale, paid services such as Darknetsearch by Kaduu or hunter.io can also be used to search for user accounts.
It is less complicated to enumerate users from an internal network (for example, in an Active Directory domain). All that is needed to do so is a valid domain user with no special authorizations.
In addition to valid Windows tools such as ADExplorer from the Sysinternals Suite or the PowerShell Active Directory module, there are also explicit attack tools for enumeration.
A small selection is listed below:
Linux:
Windows:
Password Policies – Why They Are Crucial for Password Spraying Attacks
Before the actual password spraying attack, it is advisable to check the applicable password policies, especially on internal networks. If, for example, the lockout threshold is set to five invalid login attempts, attackers would likely lock out a large number of users from the list on their sixth password spraying attempt. By knowing the guidelines, unnecessary blocks can be avoided and a targeted approach can be taken.
The password policy of a domain can be retrieved using the following tools:
Linux:
Windows:
- net accounts
Note: Depending on the hardening of an Active Directory domain, certain accounts may be assigned specific password policies. This is the case, for example, with fine grained password policies. Third-party products may also implement their own password policies, which may differ from the standard password policy. If a password spraying attack is to be carried out as part of a security audit, it is advisable to check which accounts are subject to password policies.
Carrying Out a Password Spraying Attack
Equipped with a list of valid user accounts, a password that is likely to be used by employees, and knowledge of the password policy applied, attackers can carry out the actual password spraying attack in the final step.
Depending on the attack scenario, different tools are available for this purpose as well. However, the procedure is the same for all scenarios. Attackers authenticate themselves with user names from the list always using the same password. If authentication is successful, this user is considered compromised.
Selection of tools for password spraying attacks in an Active Directory domain:
Selection of tools for password spraying attacks against externally accessible systems, such as Azure, OWA, Citrix, VPN endpoints, etc.:
The access information obtained in this way can then be used for further attacks in the context of the compromised user.
Typical Targets and Vectors of Password Spraying Attacks
As already mentioned, cybercriminals can carry out password spraying attacks on both externally accessible and internal systems. Such an attack can therefore be used to gain initial access to systems, for example in the cloud, but also at a later stage of a cyberattack.
Since authentication is still primarily based on passwords and users tend to use passwords that are easy to remember (and therefore easy to guess), password spraying attacks continue to be very popular. This is particularly evident from attacks on publicly accessible Azure and EntraID endpoints.
Sources: The Hacker News, Heise, Bitdefender
By conducting regular password audits, companies can check password security, identify vulnerabilities at an early stage, and strengthen cyber resilience in the long term with targeted measures.
The Difference Between Password Spraying and Credential Stuffing
Both password spraying and credential stuffing are among the most popular methods used by cybercriminals to take over accounts. Although the two terms are often used interchangeably, they represent two different types of attacks.
While password spraying takes advantage of the fact that many users tend to use weak or easy-to-remember passwords, credential stuffing benefits from the fact that many users reuse passwords for multiple accounts.
This can also be derived from the term “credential stuffing”, which refers to attackers using access data from breaches and “stuffing” it into all login masks. They take the combinations of email addresses or usernames and passwords that a user uses (or has used in the past) and try them out on other services. This is based on the hope that users are registered with the same email address and use the same password.
Note: A company is able to control to a certain extent whether employees reuse passwords within the company. However, it is not possible for them to check whether employees use the company password in a private context. Depending on the risk assessment, it may therefore make sense to use “darknet monitoring” to identify breaches affecting employees’ company accounts.
How to Prevent Password Spraying and Credential Stuffing?
Now that we have seen how attackers carry out password spraying attacks and what factors play a role in this, the crucial question arises: What can companies do specifically to detect and prevent such cyberattacks?
Detection Methods for Password Spraying and Credential Stuffing
Both of these types of cyberattacks are popular because they are comparatively inconspicuous. A classical brute-force attack can be identified quite quickly in the logs as there are many incorrect login attempts for an affected user account.
A password spraying attack, on the other hand, requires attackers to search for other patterns. One possibility is to look for authentication attempts by many different users within a short period of time. If these were also made from individual (or a few) IP addresses/devices, it is likely to be a password spraying attack.
Credential stuffing is more difficult to detect than password spraying as the attacks are carried out using potentially valid credentials and, at first glance, appear to be legitimate login attempts. If “darknet monitoring” is already in place, it is advisable to keep an eye out for new breaches and, if one is discovered, to search it for user accounts belonging to your own company. Suspicious login attempts to one’s own infrastructure should then be identified with the users concerned. It is also advisable to ask users to change their password.
So-called “honeypots” have also established themselves as a proactive means for detection in the internal network. These are, for example, access data of non-existent users who appear to have high authorizations (e.g., with “adm” in their name). Such access data is stored in easily accessible locations, for example, in a public network share on the internal network. As soon as attackers attempt to use these credentials in the course of a credential stuffing attack, an alarm is triggered.
As in most cases, effective detection requires extensive logging. In particular, authentication attempts must be logged for all relevant endpoints.
Prevention of Password Spraying and Credential Stuffing Attacks
Both password spraying and credential stuffing attacks can be made significantly more difficult for attackers by taking preventive measures.
The success of a password spraying attack depends on the quality of the password. It should be avoided to use popular passwords. A password audit or the Microsoft Entra Password Protection can be useful for this purpose. The latter prevents the use of weak or well-known passwords and can also be extended to include a user-defined list of keywords, such as the company name. Numerous variations of this keyword are also blocked. In addition, cybersecurity awareness trainings can help users choose secure passwords.
Password spraying attacks on external login pages can also be made more difficult by implementing a rate limit for passwords and user names. The aim should not be to lock users out after several failed login attempts in a short period of time as attackers could take advantage of this to deliberately lock users out. Instead, the time between individual requests should be gradually increased so that an automated attack would take too long.
Another recommendation to avoid password spraying, credential stuffing, and many other authentication attacks is to use a second factor whenever possible. Since attackers need to be in possession of both the password and the second factor in order to gain access, the hurdle for a successful attack increases immensely.
Furthermore, it’s always useful to check from where a resource is being accessed. Does the device match the user? Is access from this country desired?
Finally, the so-called defense-in-depth approach is recommended. This approach attempts to minimize the impact of an attack by introducing several successive layers of defense. For example, users may have been compromised by a password-spraying attack. However, as they have as few rights as possible (least privilege principle), attackers can only exploit them to a limited extent.
Conclusion: Strengthening Cybersecurity Through Awareness and Testing
Password spraying and credential stuffing attacks are widespread today and pose a serious threat to businesses. Since users often have to manage numerous accounts, the temptation to use weak passwords or reuse passwords increases, which opens a gateway for attackers. To make matters worse, such attacks are difficult to detect.
This makes it all the more important to take proactive measures. These include basic IT security principles such as using strong, unique passwords, multi-factor authentication, and a defense-in-depth approach. Combined with regular testing and awareness training, such as a Cybersecurity Awareness Escape Room, this can significantly increase resilience to password spraying and credential stuffing.
Oneconsult offers various possibilities for testing your resilience to password spraying and credential stuffing attacks. Our Penetration Testing Team supports you in identifying and eliminating vulnerabilities in authentication. Our Red Team then checks the measures implemented and carries out attacks in the same way that real actors would proceed.