Whether it’s threatened DDoS attacks, data leaks, or sextortion scams – cybercriminals often demand payment via Bitcoin wallet addresses. It’s the (supposed) anonymity of cryptocurrency that makes it particularly attractive for extortion attempts.
In this blog post you will learn how to analyze Bitcoin addresses quickly and effectively to identify typical patterns and better assess whether it is a widespread spam campaign or a targeted attack. With this knowledge you can support your employees and improve the incident response process in your company.
Table of contents
Bitcoin as a Popular Means of Payment for Cyber Fraud
Both private individuals and companies keep receiving various types of blackmail letters via digital communication channels, especially via email. Companies are threatened with, e.g., a distributed denial-of-service attack (DDoS) or the compromise of their website and the resulting theft of trade secrets. Supposedly, only the payment of a predetermined amount of Bitcoins to a wallet (which is comparable to a bank account) can protect the company from such an attack.
Private individuals often experience a form of sextortion with the request to transfer a certain amount to a Bitcoin wallet. Sextortion means the threat of publishing nude photos or videos.
Note: If you are in Swiss, Germany or Austria and you or your employees receive such a sextortion email, we recommend consulting the official information pages:
- Swiss Crime Prevention (available in German only)
- Police Crime Prevention by the Federal States and the Federal Government (Germany; available in German only)
- Criminal Intelligence Service Austria (available in German only)
Why Choosing Bitcoin as a Means of Payment?
Bitcoin is the preferred payment method of cyber criminals for several reasons. Compared to traditional payment methods, it provides them with one decisive advantage: pseudonymity. This means that personal information is replaced by placeholders or removed entirely. Although all Bitcoin activities are publicly visible, only the wallet addresses of sender and recipient appear in the transaction list – and it’s not possible to trace them back to real people easily.
Additional measures, such as the use of so-called Bitcoin mixers, can further conceal the traces of transactions. This is why Bitcoins are virtually anonymous which makes investigations considerably more difficult, though not impossible.
Furthermore, it is quite easy for victims of cyberattacks to acquire Bitcoins, especially when it comes to smaller amounts. This reduces the inhibition threshold for making payments and thus increases the likelihood that the attackers’ demands will be met.
Using the Bitcoin Address for an Initial Assessment
The Oneconsult International Computer Security Incident Response Team (CSIRT) is regularly contacted by companies that receive such blackmail letters by email. They are often unsure whether it is a targeted attack so the threatening email should be taken seriously, or whether it is mass email, i.e., email spam. Using the case study below, we will show you how you can use the Bitcoin address sent to you to get some initial answers to this question.
Step 1: Identifying the Bitcoin Wallet Address
Bitcoin wallet addresses and publicly available information about them can provide valuable hints. Therefore, the first step is to identify the wallet address contained in the message.
In the following sample message such a Bitcoin wallet address is marked in red:
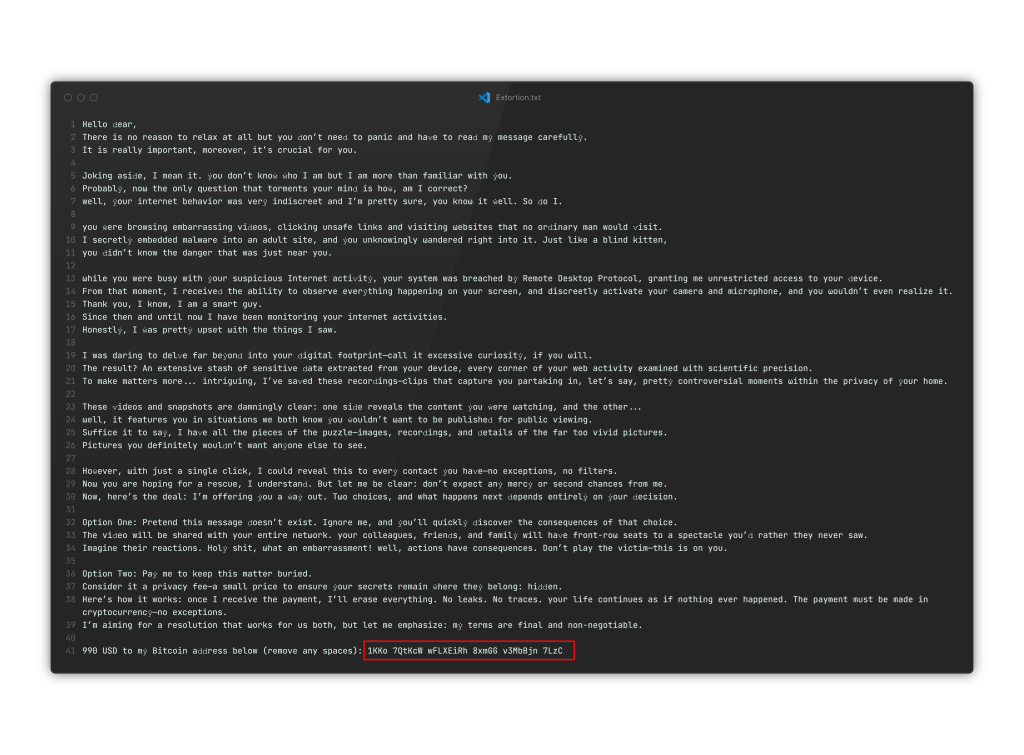
After identifying the address, we conduct an initial brief investigation prior to analyzing the email in detail.
Step 2: Brief Investigation on the Bitcoin Wallet Address
For such brief investigations there are a variety of free and paid services that link Bitcoin wallet addresses to known extortion attempts, ransomware campaigns, or other criminal activities.
These services are generally based on user reports and publicly available sources. Therefore, our team consciously uses a combination of several platforms to maximize the chances of finding meaningful results. The tools and websites we use include, among others:
- https://www.chainabuse.com/
- https://www.ransomlook.io/crypto
- https://bitcoinais.com/
- https://bitcoinwhoswho.com/
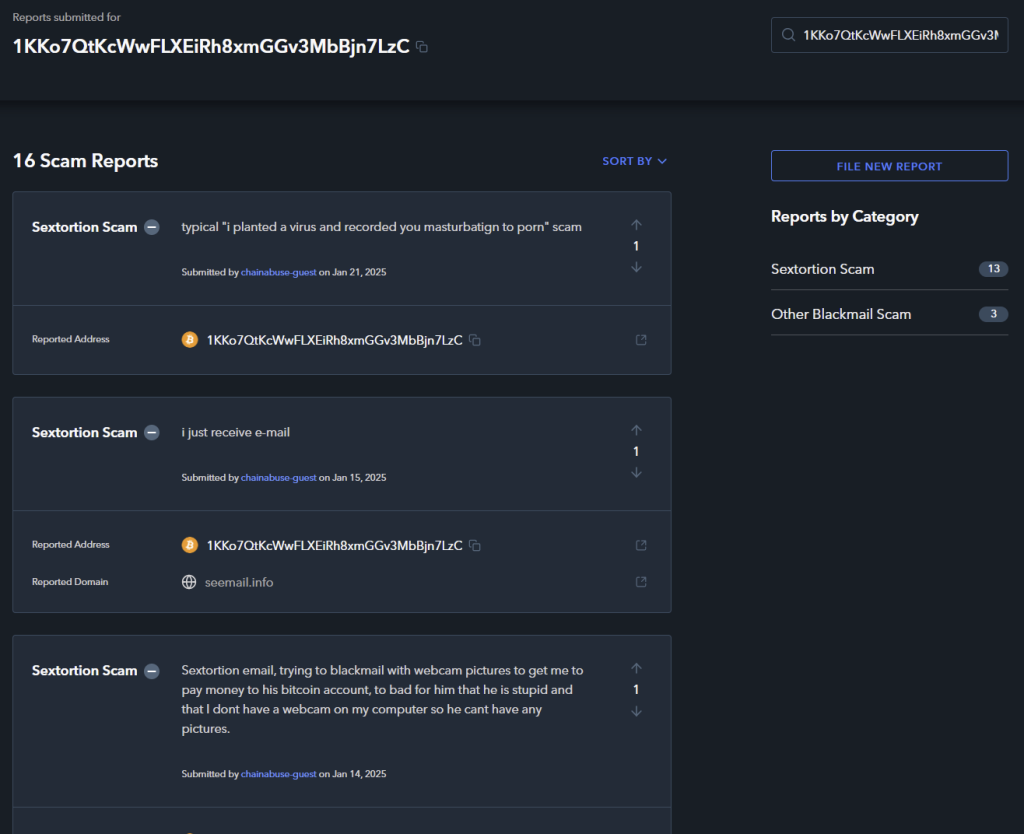
So based on our example, we first search for the Bitcoin wallet address “1KKo7QtKcWwFLXEiRh8xmGGv3MbBjn7LzC” on the Chainabuse website (the search field is located at the top left of the website) immediately leading to the following result:
Step 3: Comparing Existing Reports With the Message Received
The Chainabuse platform provides us with various user reports on the Bitcoin wallet address we are looking for. In this case, we can see summaries of the emails in the descriptions and compare them with the email received.
In doing so, we note that the reports correspond to the email received.
- A total of 16 “reports” are associated with the Bitcoin wallet address. This means that other recipients have received emails with the same or similar content.
- The same Bitcoin wallet address was used multiple times instead of using a unique address for each recipient. This makes it difficult for extortionists to distinguish between people who have paid and those who have not.
This makes it highly likely that the email is a mass email, i.e., spam, and can therefore be ignored.
Conclusion: A Simple Analysis Brings a Lot of Clarity
So, if you receive a Bitcoin wallet address, it is worth looking at the services listed above. With very little effort this can quickly provide you with additional information for assessing the situation at hand and thus offers you useful assistance.