Batch files are an essential tool many users and administrators use to perform automated tasks. However, attackers also use these batch files to execute malicious commands on a system. To avoid detection by antivirus software, batch files are obfuscated.
Obfuscation is a method that attackers commonly use to disguise their malicious files or payloads. Our Digital Forensics & Incident Response Team often encounters this. Obfuscation has two main goals. First, from a defender’s perspective, more resources must be invested to understand how the malware works. Second, obfuscation is intended to circumvent protection mechanisms such as antivirus. There are a variety of techniques to achieve obfuscation. This blog post describes what batch files are and why they are obfuscated.

Table of contents
What is a Batch File?
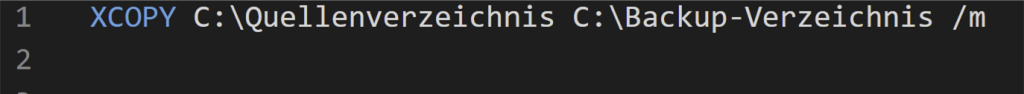
A batch file (.bat) is an executable text file that is run by the Windows command line processor cmd.exe (CMD). These files can be created with any text editor and contain CMD commands. Double-clicking on such a file opens the command line, processing its commands from top to bottom. Administrators often use batch files to execute certain workflows faster and easier, eliminating the need to enter the commands manually. Figure 1 shows a simple batch file that uses the XCOPY command to copy the contents from the source directory to the backup directory. Specifying the “/m” flag ensures that only updated files are copied, preventing files that have already been backed up from being copied again.
Why are Batch Files Obfuscated?
Like administrators, attackers also use .bat files because they can be used to execute many system-specific commands. An example of this is disabling Windows Defender. As shown in Figure 1, a batch script is plain text, and Signature-based antivirus software can scan these files and check for malicious content. This results in these malicious batch files being detected and blocked by the above solutions. To prevent this, the attackers often obfuscate the content. Various techniques can be used for this obfuscation, and there are several freely available and easy-to-use implementations of obfuscation techniques. They are also built into common tools such as Meterpreter (see Metasploit Documentation). Figure 2 shows an obfuscated batch file. The content consists of seemingly random characters which hide the actual function of this file.

How Can I Detect Batch File Obfuscation?
When obfuscated, some antivirus solutions can no longer detect malicious batch files. Therefore, caution is advised when such executable files are found that have content that is difficult for humans to read. Under no circumstances should these files be executed before the file is thoroughly reviewed. Likewise, care should be taken if batch files are found in an unexpected location, such as on the desktop, or if no batch files are expected on the system. The following methods can be used to detect batch file obfuscation:
Text Editor
The easiest way to view the contents is to open the file in a text editor. To detect possible obfuscation, the following points can be considered:
- Are the characters readable to me? As shown in the example in Figure 2, these are unknown characters that cannot be interpreted by humans. It is also possible that only part of the content is not readable. Again, an eye should be kept on this.
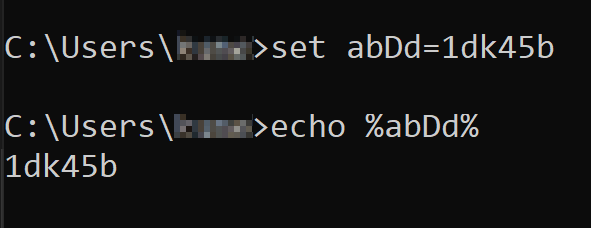
- Are randomly generated variable and function names used? An example can be seen in Figure 3. Set is used here for setting a variable.
- Also noticeable is when existing functions are assigned to a new variable name.
If the mentioned points are recognized, it can be a possible obfuscation. The file should be checked further and only then executed.
YARA Rules
YARA rules offer another possibility for detection (see Security Insider). YARA rules can be used to search for specific patterns in files or processes. This should make it possible to detect and classify malware. There are already many predefined rules that can be used. However, it is also possible to write your own YARA rules. Additionally, YARA rules can be used in different antivirus solutions It should be noted that what can be detected depends heavily on the rule in question. There are YARA rules that are written for a specific obfuscator. This rule only works for that obfuscator and does not detect other techniques. However, there are also rules that work for multiple techniques. Therefore, YARA rules are limited in their ability to detect batch file obfuscation.
To demonstrate the use of YARA rules, a simple rule was written. As shown in Figure 4, this rule searches for the three specified hexadecimal values (see red marker). One of the three values must be contained in an obfuscated batch file to be recognized. Please note that this is an example rule and should not be used in practice.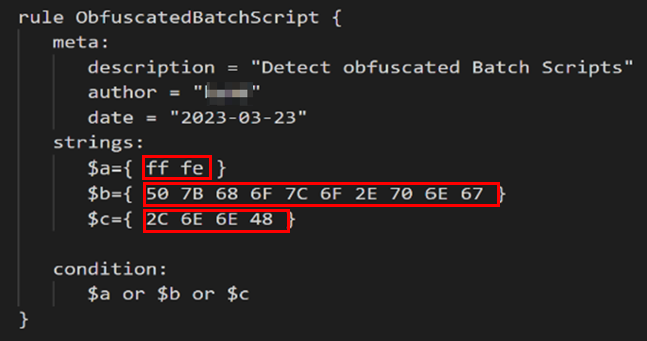
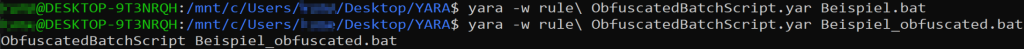
Figure 1 shows the original script without obfuscation and Figure 5 represents the obfuscated version of the script. The obfuscation was performed using an obfuscator available on the Internet (see github). This obfuscation is now to be detected using the example YARA rule.
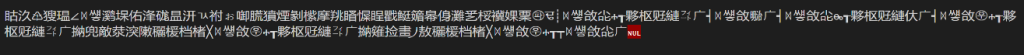
The rule is applied to the two files with the command yara. As can be seen, nothing is detected in the Beispiel.bat file. Obfuscation is detected in the Beispiel_obfuscated.bat file and thus the rule is applied.
Outlook
The obfuscation of batch files is a way for attackers to bypass a company’s security measures. In the upcoming second part, an obfuscation will be presented from a real case, and it will be shown how suspicious batch files were handled and how the obfuscation can be reversed.
Do you still have questions about Batch File Obfuscation or need assistance with it? Our DFIR team will be happy to help you. We look forward to hearing from you.





