Preparation with a comprehensive checklist is central to managing a cyber incident. To ensure that nothing is forgotten during the stressful situation, all departments of a company must be informed about their tasks and duties in advance.
Contrary to what many believe, a cyber attack is not just a problem for the IT department. It affects and requires collaboration from many different areas of a company, including but not restricted to the management, communications, and the legal department.
Table of contents
The goal of this 360-degree checklist is to provide an overview of what needs to be considered during a cyber attack and the responsibilities and tasks of all individuals involved. It is based on the six phases of the SANS Institute’s Incident Response (IR) process: preparation, identification, containment, eradication, recovery, and learned lessons.
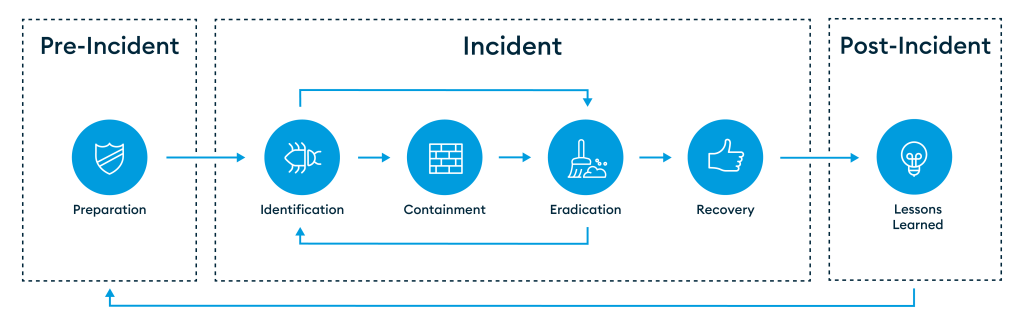
The Oneconsult International Computer Security Incident Response Team (OCINT-CSIRT) uses the checklist in collaboration with IT departments during incidents. The checklist includes not only technical but also organizational tasks and provides a foundation. However, in order for it to be suitable for your own company, it needs to be adapted. The tasks are listed in a rough order. This is because the incident response process is a cycle with many feedback loops, which is why it is not possible to list the various tasks in a linear fashion.
The 360 Degree Checklist
Phase 1: Preparation
The first phase of the incident response process consists of defining and implementing technical and organizational processes and measures for the event of a cyber incident. The aim is to prevent an attack from happening in the first place and to be able to recover as quickly as possible if an attack does occur.
Technical
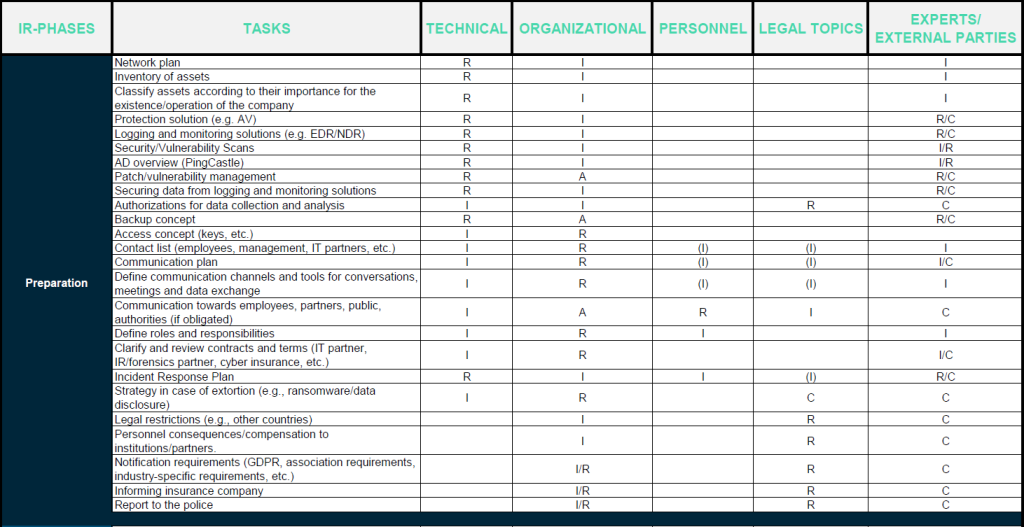
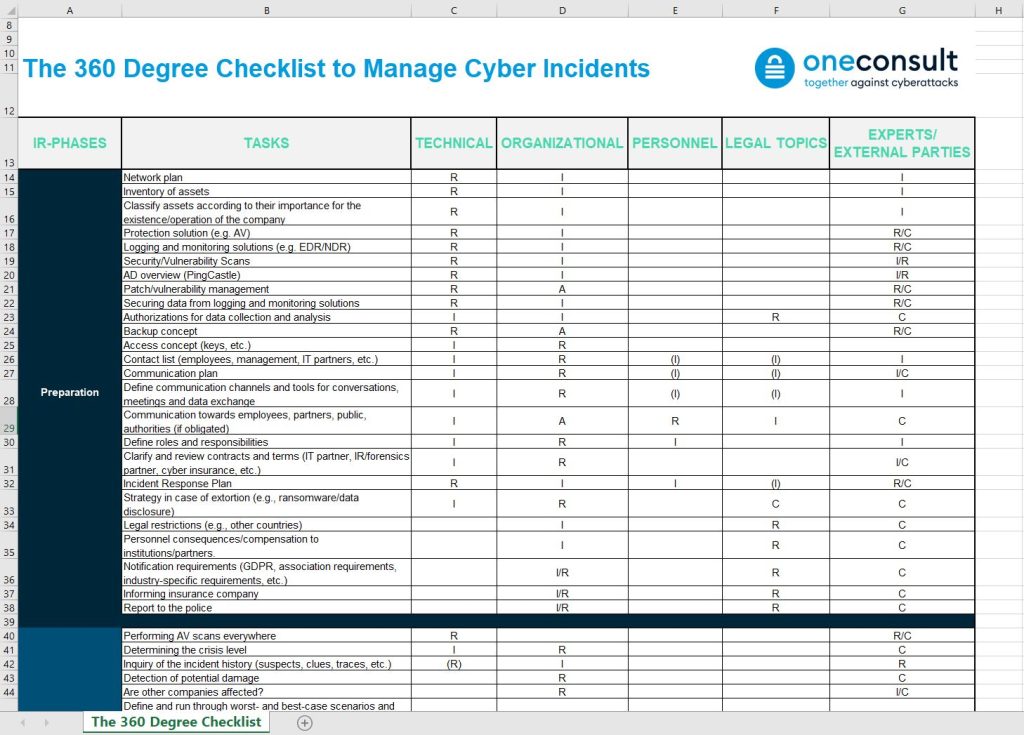
On a technical level, it is necessary to create a network plan and an inventory of assets, as well as to prioritize them. Such an inventory can be very useful for both forensic analysis and reconstruction. To be best protected and have a good overview, a protection solution (e.g., antivirus, Endpoint Detection and Response (EDR)) should be deployed, and regular vulnerability scans should be performed. The Active Directory should also be checked on an ongoing basis. The free tool “PingCastle” is recommended for this purpose. It should also be ensured that all necessary tools and resources are available. In addition, it is recommended to implement a patch/vulnerability management. A backup concept is also recommended to determine which data should be backed up where, how and how often.
Organizational
At the organizational level, it is necessary to start by defining a contact list and communication channels and tools. For the event of a crisis, it should also be defined who (employees, management, customers, suppliers, authorities, the public, etc.) must be informed when (daily, weekly, in the event of an incident, etc.) and in what form (verbally, in writing, by email, etc.). This can for example be written down in a communication plan. It is also highly recommended to create an incident response plan. In this plan, roles and responsibilities are defined and it is also determined how to respond depending on the criticality of the security event (incident vs. crisis). If you need such an incident response plan, we are happy to create it for you. In addition, a strategy in case of extortion (e.g., ransomware after encryption, threat of data disclosure) can be developed in advance. It should also be ensured that the necessary contacts are available in case of need (IR/forensics partner, etc.) and that these are contractually regulated if necessary. Possible obligations to notify (e.g., DSGVO) and inform (insurance, customers, suppliers, etc.) should also already be known.
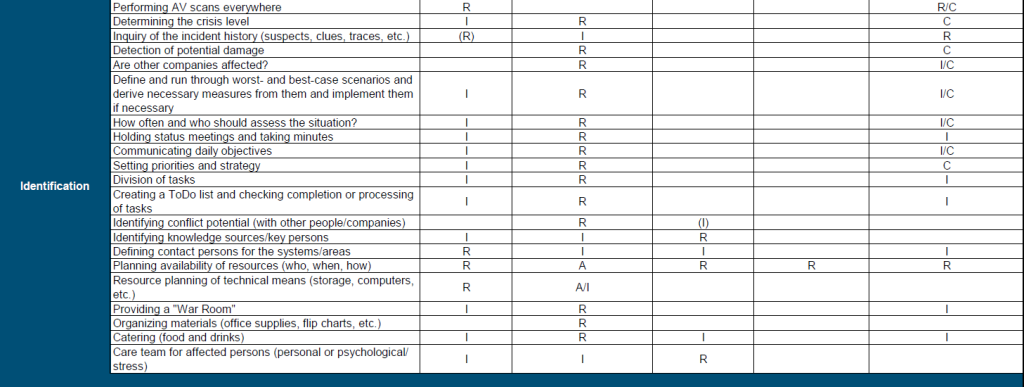
Phase 2: Identification
Technical
As of this phase, the company is a victim of a cyber attack. The goal of this phase is to identify the incident and obtain as much information as possible to determine the extent and impact. The current state of the crisis and all information already available should be discussed with all parties involved during status meetings. The objectives for the day, priorities and strategies, and the distribution of tasks should be determined during these meetings. Worst and best case scenarios can also be defined in order to derive measures from them.
Organizational
In terms of organization, physical and personnel resources should also be available. Therefore, the availability of people and the provision of a room, equipment and catering should be clarified.
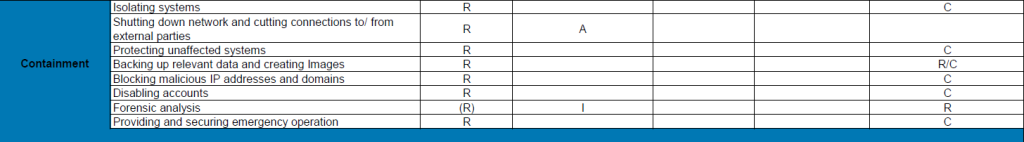
Phase 3: Containment
In the containment phase, the goal is to prevent the attacker from moving through the network and thus minimize the damage. Therefore, at this stage it should be clear which systems are already infected. The affected systems should immediately be isolated, i.e., pulled from the network, and the data (logs, etc.) backed up for analysis. It is important to protect the clean systems as well, especially the backups. In addition, connections to and from external partners or sites should be disconnected. Any Indicators of Compromise (IOCs) already found by the forensic analysis, such as IP addresses and domains, should also be blocked, and compromised accounts should be deactivated. Emergency operations can be set up so that employees can continue to work, albeit on a reduced basis.
Phase 4: Eradication
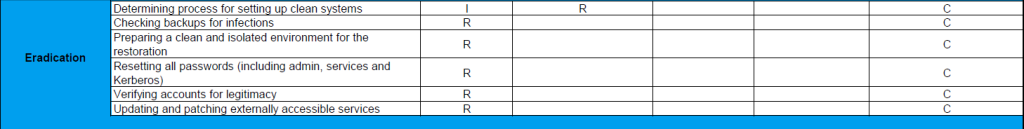
During the eradication phase, the attacker is removed from the network and everything they have done is cleaned up. In some cases, it is an option to change the password to lock out the attacker. Resetting all passwords (including admin, services and Kerberos) is recommended especially in incidents like ransomware, where the Active Directory has been compromised. The legitimacy of user accounts also needs to be verified, as attackers can also create new accounts. A recovery strategy is implemented within a clean and isolated environment which was prepared for this purpose. In addition, backups should be checked for infections. The externally accessible services that were previously shut down are patched and put back into operation.
Phase 5: Recovery
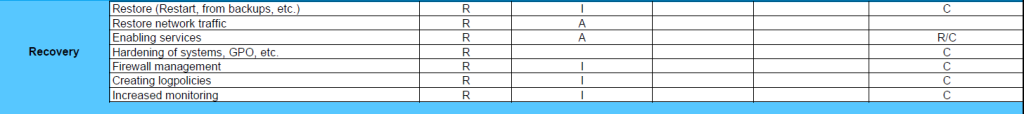
At this point, the goal is to return to normal operations with as little damage as possible. Here, the systems and data are restored from the backups if these are clean, otherwise they are rebuilt. The network will also be restored. It is therefore important to increase security during this phase, which can be done by hardening systems and Group Policy Objects (GPOs), creating log policies and managing the firewall. The new environment should also be heavily monitored in case a remnant has lingered so that immediate action can be taken.
Phase 6: Learned Lessons
After the case is closed, it is important to prepare a report documenting, among other things, the results of the analysis and the measures taken. This is then distributed to the necessary people (management, etc.). Afterwards, a debriefing should take place with all parties involved to draw the lessons from the incident. It should be discussed what went well and what could have gone better, what further measures should be taken and where processes need to be adjusted and improved. Minutes of the meeting should also be taken and deadlines should be set for the implementation of the measures.

Structure of the 360 Degree Checklist
The checklist is presented in the form of a RACI matrix :
- R: Responsible – Who (which person, role, organizational department) performs the task?
- A: Accountable – Who decides and has overall responsibility or will report to performing the task correctly?
- C: Consulted – Who can advise and support with expertise?
- I: Informed – Who must be informed, who can request information?
The checklist includes the following five topics:
- Technical: relevant for the technical departments (e.g., IT)
- Organization: taskforce
- Personnel: mainly HR
- Legal topics: lawyers, attorneys
- Experts/external parties: IT partners, IR/forensics partners (e.g., Oneconsult)
The table is read in the following way, e.g. for the first row (network plan):
- – The IT department (technical) creates a network plan during the preparation phase to achieve an overview.
- – The network plan is made available to the task force (organization) and the experts/external parties during the assignment.
Conclusion
In order to be optimally prepared for a cyber incident and to ensure that nothing is forgotten in an emergency, the creation of such a checklist is highly recommended. Therefore, we are happy to provide you with the Oneconsult 360 Degree Checklist for dealing with a cyber incident:
Download 360 Degree List Overview PDF

Download 360 degree list as Excel
This checklist serves as a basis. It should be adapted to your own company. Our Incident Response Team will be happy to support you and clarify any questions.




