As Microsoft services move to the cloud, Azure Active Directory (Azure AD) and Microsoft 365 (M365) are becoming popular targets for attackers. Threat hunting can help uncover signs of compromise early on.

Cybercriminals are always keen to know the latest trends in the IT world in order to constantly develop new opportunities for attacks. The migration of Microsoft services to the cloud has also turned attackers’ focus to Azure AD and M365. A popular attack scenario is the compromise of a user account. Such an attack can easily go undetected for a long time if the systems are not actively monitored. Threat hunting starts exactly at this point by actively looking for indicators of compromise. This article shows what to look for and explains the possible consequences of such a compromise.
Attack on The User Account
Microsoft’s identity services are vulnerable in many ways. The nature of a cloud solution is that it is accessible to all from the Internet. If an attacker obtains a user’s credentials, they can use them to log into the cloud themselves and wreak havoc in the environment.
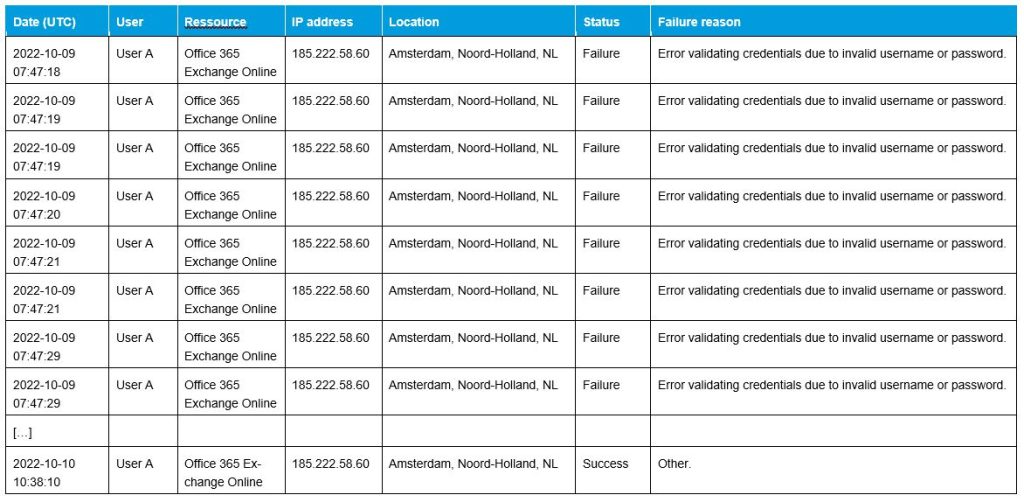
Phishing, brute force or password-spraying attacks are the three most common ways to obtain these credentials. In a brute-force attack, the attacker tries to guess the password through trial and error. A password-spraying attack is a type of brute force, but without attracting attention or locking the user out through multiple failed logins. This can be achieved by trying popular passwords across many users. Brute-force attacks are clearly evident in the Azure AD Portal sign-in log files. Particularly suspicious are multiple failed login attempts in a short period. If this is followed by a successful login not originating from a known IP address, the user has most likely been compromised. Figure 1 shows a series of failed logins from the Netherlands within a few seconds. This is only an excerpt from an incident; the attack lasted several days until it was finally successful.
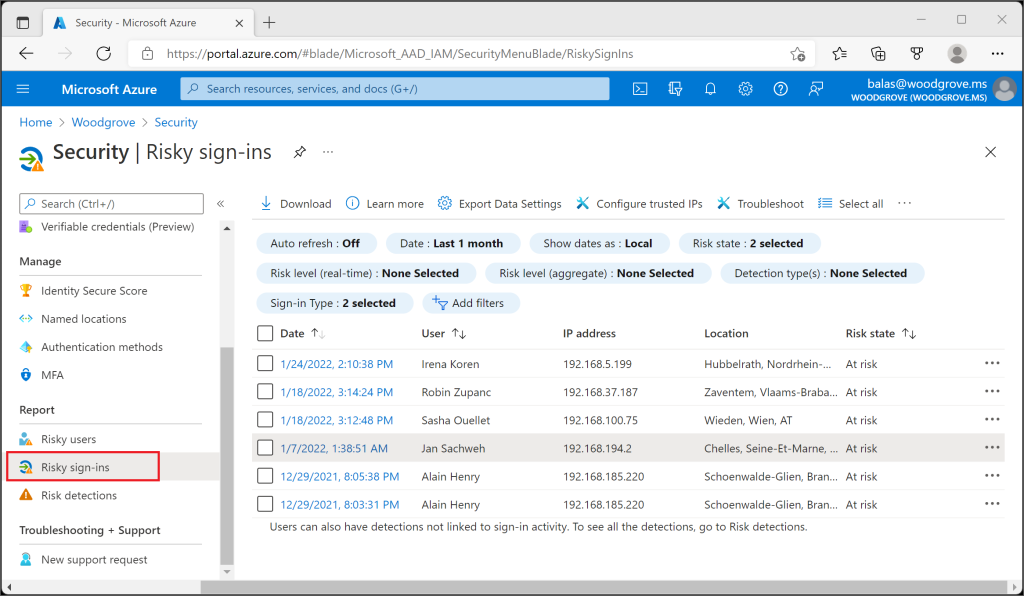
In comparison, a password-spraying attack is more inconspicuous, as is a login with credentials obtained through phishing. However, such events can also be identified in the log data. The Azure AD itself has implemented aids that highlight anomalies in the logins. In the Risky Sign-ins or Risky Users area of the Azure AD portal (see Figure 2), unusual logins are documented based on, for example, geolocation, the IP used or the browser used (see Microsoft Learn, What a risk?).
In addition to the obvious artifacts such as failed logins, it is also worth assessing other information in the log files. If logins from another country suddenly occur, which cannot be explained by travel activities, it should be checked whether this can be explained by the use of a virtual private network (VPN). It is also documented in the logs from which device the user logs in. Sudden changes in the operating system or browser version can also be suspicious.
If an attacker succeeds in obtaining access credentials, he has access to all available Microsoft cloud services due to the interconnectedness. The only restriction is the permissions assigned to the user.
Let the Hunt Begin
To know which artifacts to look out for, it is essential to know the current threat situation. The interests of cybercriminals can be quite different once they have gained access to the Microsoft cloud environment. In the following sections, different approaches and threats are described in detail.
To perform threat hunting in the Microsoft Cloud environment, a user with Global Reader and Security Reader rights is required. This also makes it possible to view the Unified Audit Logs (UAL) and export them for further analysis. The UALs are of great importance for forensic investigation, as they are a collection of all logs of the individual services in the Microsoft 365 environment.
User Manipulation
When a user has been compromised, the attacker has access to his account and various online services. This can be exploited to manipulate user accounts within the scope of the granted permission. New users or groups can be created, and users can be added to or removed from groups. Forwarding rules, mailbox rules, or mailbox delegations can also be set up in Exchange Online. All these activities allow the attacker to continue controlling the compromised user without necessarily having to actively log in with their credentials. This allows the compromise to be disguised while establishing persistence. An attacker also can add new applications, devices, or even a new multifactor device to Azure AD for authentication.
All of these activities can be tracked in the UAL. A selection of interesting entries is listed below:
- Field “operations”, value “Add user.”
- Field “operations”, value “Update user.”
- Field “operations”, value “Add member to group.”
- Field “parameters.ForwardingSmtpAddress.keyword”
- Field “operations”, value “New-InboxRule”
This refers to Mitre Att&ck Technique T1098: Account Manipulation.
Data Exfiltration
An attacker can use the gained access to the Microsoft Cloud to collect information. This can be done using the Microsoft Graph API (see Microsoft Developer), which makes it possible to access the extensive data volume of the Microsoft 365 platform with targeted queries. This information can be useful in another attack, or the victim is blackmailed under the threat that the data will be publicized. Data extraction can be done by setting up forwarding rules in Exchange Online or downloading directly from OneDrive or SharePoint. The file download can be seen in the UAL in the “operations” field with the value “FileDownloaded”.
This refers to the Mitre Att&ck Techniques T1114: Email Collection and T1213: Data from Information Repositories.
Email Abuse
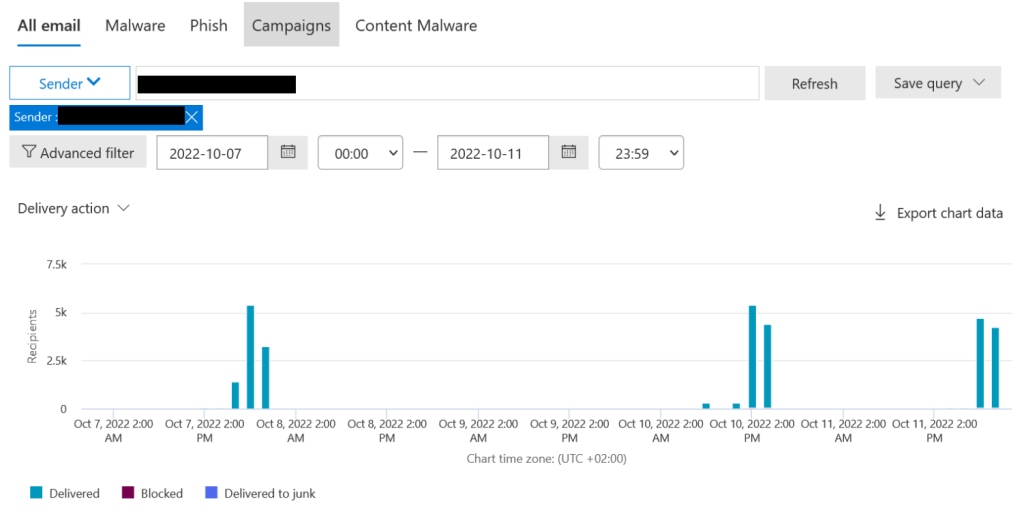
If a user has been compromised, the attacker can log on to the Exchange Online service with this user. He thus has access to a legitimate email account, which he can use for further attacks. For example, a phishing campaign can be launched from the email account (see National Cyber Security Center: Phishing, Vishing, Smishing). This can be seen in the Windows Defender portal when the number of emails sent is significantly higher than the average (see Figure 3). In this example, over 5,000 emails were sent from a compromised user on some days.
With the help of a mailbox rule, the traces of these attacks are obfuscated, by moving them directly to the trash and deleting them.
Another attack scenario is a “Business Email Compromise” (BEC) (see National Cyber Security Center, Billing Manipulation Fraud (BEC Fraud)). If the compromised user has been involved with billing in the past, this can be used to redirect future payments to a third-party account. This includes payments to and from the affected company.
This refers to Mitre Att&ck Techniques T1566: Phishing, T1087: Account Discovery, and T1564: Hide Artifacts.
A User Has Been Compromised – Now What?
If evidence of compromise was found during the Threat Hunting, several immediate actions should be implemented:
- Reset the password of the compromised user and terminate their active sessions. This can ensure that direct access to the user account is blocked.
- Set up multifactor authentication (MFA) if it is not already in place, or check existing MFA devices.
Note that it is also possible to bypass MFA with an MFA fatigue attack. In this case, the user is inundated with push messages from the authenticator app in the hope that one of them will be accepted. This risk can be prevented by requiring code input from the authenticator app instead of push messages (see Microsoft Tech Community, Defend your users from MFA fatigue attacks).
The next step is to check what activities have been performed with the compromised user. Rules that have been set up should be deleted and user manipulations, such as adding an MFA device, should be reversed. Over the next few days, the previously compromised user should be monitored regularly to ensure that all this risk has been fully mitigated.
If the compromised user was an administrator, the extent of the attack is greater because more actions can be performed with administrative rights, such as creating new users or changing configurations. Administrator accounts should therefore be particularly protected.
A User Has Been Compromised – Now What?
Attacks on the Microsoft cloud environment are steadily increasing. An attacker can use compromised users to extend their rights in the company’s cloud environment, leak data, or use the legitimate mailbox for further attacks such as phishing campaigns. With the help of threat hunting, signs of a compromised user can be detected early, and further damage can be prevented.
Do you still have questions or would like our support? The Digital Forensics and Incident Response Team is happy to help. We look forward to hearing from you!





