IoTGoat is intentionally vulnerable software, like that found on routers for example.
Included are the most common vulnerabilities of IoT devices. The project serves to raise awareness of these vulnerabilities in order to make future generations of IoT devices and networks more secure. This article introduces both the project in general and some of the vulnerabilities.

Figure 1: IoTGoat
The non-profit organization Open Web Application Security Project (OWASP) is best known for compiling the “OWASP Top 10”, a list of the most common security vulnerabilities in web applications.
However, OWASP’s work goes beyond this: On the one hand, the organization creates standards, guidelines and guidance on various security-related topics; on the other hand, it is involved in the development or collection of tools that can be used to check and improve security mechanisms in applications. [1]
Of all the tools, the “Juice Shop” web application, a store application that contains a large number of common security vulnerabilities, gained particular notoriety. The open-source software serves as a training platform or demo application for awareness training. It covers both simple attacks such as guessing weak passwords (e.g. the famous “123456”) and more sophisticated vulnerabilities such as blind SQL injections.
Since the Internet of Things (IoT) has increasingly become the focus of security researchers and criminals in recent years, OWASP has also developed an environment analogous to the “Juice Shop”. This is software such as can be found on routers or other devices with comparatively weak hardware. This firmware, which is based on OpenWrt [2], contains the most common security vulnerabilities found in the IoT (see OWASP IoT Top 10 – Part 1 and OWASP IoT Top 10 – Part 2).
In the following, we briefly discuss the general scope of IoTGoat. Additionally, two of the vulnerability groups included are presented.
The vulnerabilities, referred to as “Challenges”, are:
- No 1: Weak, Guessable, or Hardcoded Passwords
- No 2: Insecure Network Services
- No 3: Insecure Ecosystem Interfaces
- No 4: Lack of Secure Update Mechanism
- No 5: Use of Insecure or Outdated Components
- No 6: Insufficient Privacy Protection
- No 7: Insecure Data Transfer and Storage
- No 8: Lack of Device Management
- No 9: Insecure Default Settings
- No 10: Lack of Physical Hardening [3]
Each of the challenges contains several examples of the corresponding vulnerability.
IoTGoat is released via several files: [4]
- precompiled firmware
- as a virtual machine disk
- disk image file for Raspberry Pi
The different release files are designed for different application purposes. For example, the version that is available as precompiled firmware should be chosen for analyses of configuration files and individual software components.
To perform a classic penetration test, a version prepared as a VMware image can be used. After importing and starting the image provided via GitHub, the initial interface can be accessed via the automatically assigned IP using a browser:
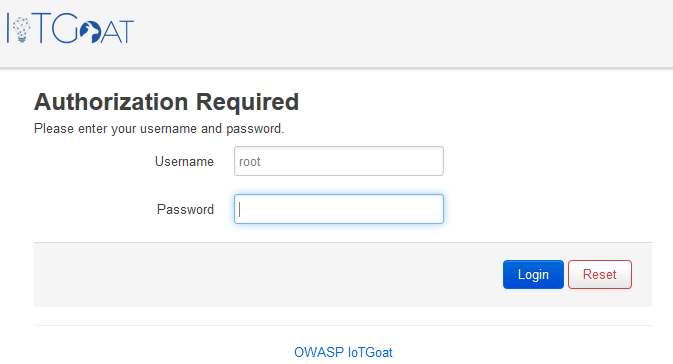
The web interface represents the first opportunity for an attack. This attack vector requires a prior analysis of the firmware. The password for the web interface is hardcoded in the firmware – an example that is also frequently encountered in reality. Instead of generating strong passwords for all devices in a production batch, a password is set once. The firmware is then applied equally to all devices. In some cases, the user is advised to change the password the first time it is used. However, if this change is optional and not a fixed requirement, a large proportion of devices remain vulnerable to this type of attack.
The initial effort is therefore comparatively high, since analysis tools have to be used to search for passwords in the firmware. In more recent devices, encryption is also used more frequently or passwords are only stored as a hash. If an attacker gains physical access to the device, however, the passwords can be extracted with somewhat more effort in this case as well.
Despite the relatively high effort, this type of attack can often prove to be worthwhile, as access data to a large number of identical devices can be gained.
However, it is not only web interfaces that are poorly secured in this way. Instead of making the initial effort to determine passwords themselves, people usually fall back on already known lists.
One such critical vulnerability can be discovered via the SSH access of the IoTGoat firmware. Initially, the username is required for exploitation. Often default usernames are not changed, thus names like “root” or “admin” can often be assumed.
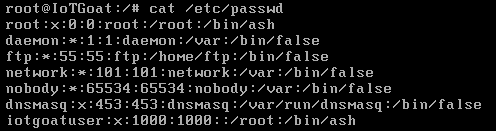
For an attack via SSH, the user “iotgoatuser” can be used, for example. Using a common password list, different credentials can be tried using automated tools. In the field of IoT, the password list of the Mirai botnet provides a high hit rate. The list is available for download on GitHub: https://github.com/securing/mirai_credentials/blob/master/mirai_creds.txt.
Using this list, automated login attempts can be made using brute-force tools such as Hydra or Medusa. These tools automatically perform a large number of login attempts using the password list provided. If one of the accesses is active, the tool reports this attempt. In the example of IoTGoat, the password list, which is only 62 lines long, quickly discovers the correct password; the following is the output from Hydra: [5]
[DATA] attacking ssh://192.168.157.128:22/[22][ssh] host: 192.168.157.128 login: iotgoatuser password: 7u**********1 of 1 target successfully completed, 1 valid password found
With this password you can now connect to the system via SSH:
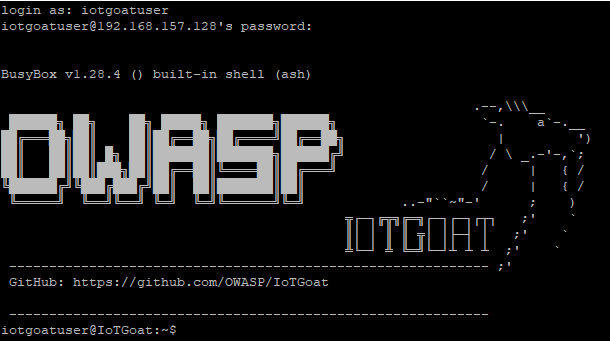
Thus, this vulnerability can be exploited using easily accessible tools and very little time.
The next group of vulnerabilities presented in this blog article covers the “Insecure Ecosystem Interfaces” item from the OWASP IoT Top 10.
In IoTGoat, as an example of this, a developer page is accessible via the web interface, among other things, on which diagnostic data is displayed and which offers certain management functions. The access protection of this page is problematic. Only a user login is required. Knowing the path to the page is then sufficient to access the management console. With the special management function, this results in a shell environment, which is tantamount to compromising the server.
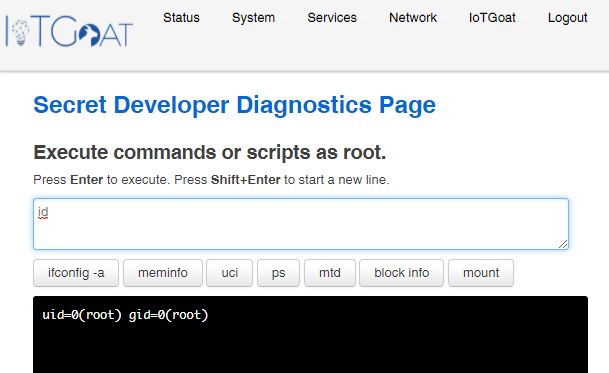
In this case, the corresponding path (cgi-bin/luci/admin/iotgoat/cmdinject) can initially only be found again with a reasonable amount of time by analysing the firmware. However, even in this case, this effort only needs to be made once for each manufacturer or product. The paths found are usually quickly compiled into lists and published by attackers.
In addition to this web interface, IoTGoat also shows the dangers of less obvious managing access: an unneeded open port 5515. If you now try to connect to this port, you have gained access to the system:
nc -nv 192.168.157.128 5515Connection to 192.168.157.128 port 5515 [tcp/*] succeeded![***]Successfully Connected to IoTGoat's Backdoor[***]
There are numerous examples of such backdoors. For example, there are several cases where well-known network equipment vendors had to provide updates for routers, switches or firewalls because such access points were discovered.
Many of the vulnerabilities identified by IoTGoat can also be found in this form in reality. However, since the focus is also on challenges that can be solved by beginners, the gaps or attacks that can actually be found are usually somewhat more complex or can only be exploited by combining several vulnerabilities.
An analogy to the IoTGoat backdoor on the managing port is, for example, a vulnerability in routers from a well-known network supplier, where exploitation was only made possible by analysing the firmware. Here, hard-coded access data had to be read out, which could then be used to connect to the managing port. However, IoTGoat only shows unencrypted access without necessary authentication.
Conclusion
Due to the different levels of possible attacks, IoTGoat is on the one hand recommendable for security researchers, as more complex analysis options and attacks are also presented. On the other hand, it can also be a worthwhile tool for private users. For example, if you are dealing with the topic of home automation, the most critical potential configuration errors are addressed using simple challenges. Despite the slight abstraction and simplification of gaps, vulnerabilities are highlighted that also occur in this way in everyday penetration tests of websites and, in particular, IoT applications.



