The vast majority of companies nowadays use Windows and therefore Active Directory. The default settings are often designed for functionality rather than security. Also, when an environment has grown over the years, misconfigurations can easily creep in. In addition, weak passwords also compromise its security. All this can make it easy for attackers once initial access to the Active Directory is gained.
How can you protect yourself? Find such misconfigurations and weak passwords yourself with appropriate tools in your Active Directory before attackers do!

Table of contents
Trust vs. Control: The Dilemma of Using Online Tools
If you want to examine your own infrastructure, you should have an offline backup of all relevant data – just in case. Besides, sooner or later you will face the question whether a tool or code from the internet is trustworthy and can be executed on the internal network. Trust is good, but control is better in this case. If, for example, the source code is available, a review can verify that only the promised functionality is included.
Presumably, defensive measures such as Microsoft Defender or PowerShell execution policies will interfere with the execution of appropriate tools and code. These should be temporarily deactivated in consultation with the system administrators for the self-audit of one’s own Active Directory.
Increasing the Security of Active Directory With Pingcastle
There are several tools, such as PingCastle and Purple Knight, that can help you identify misconfigurations and other vulnerabilities in your own Active Directory (AD). In the following, we will take a look at PingCastle as an example.
PingCastle is developed by Vincent Le Touc and has been available since 2017. It is licensed under both a proprietary license and the Non-Profit Open Software License 3.0 – so organizations can use PingCastle against their own AD environment for free. The current version of PingCastle is available for download from the website. A clear documentation of the various functionalities can also be found there.
PingCastle’s standard Healthcheck runs through relatively quickly, even in large, complex AD environments:
PS > .\PingCastle.exe --healthcheck --no-enum-limit
PingCastle delivers the results as an interactive HTML file and can be viewed in the web browser. The risk level of the scanned domain is given as a numerical value between 0 and 100, where 100 describes the highest risk level. The risk level is the maximum of the risk levels of the four indicators used by PingCastle: operations related to user and computer objects (Stale Objects), trust relationships between different Active Directories (Trusts), Privileged Accounts, and all security aspects that do not fit into any of the previous categories (Anomalies).
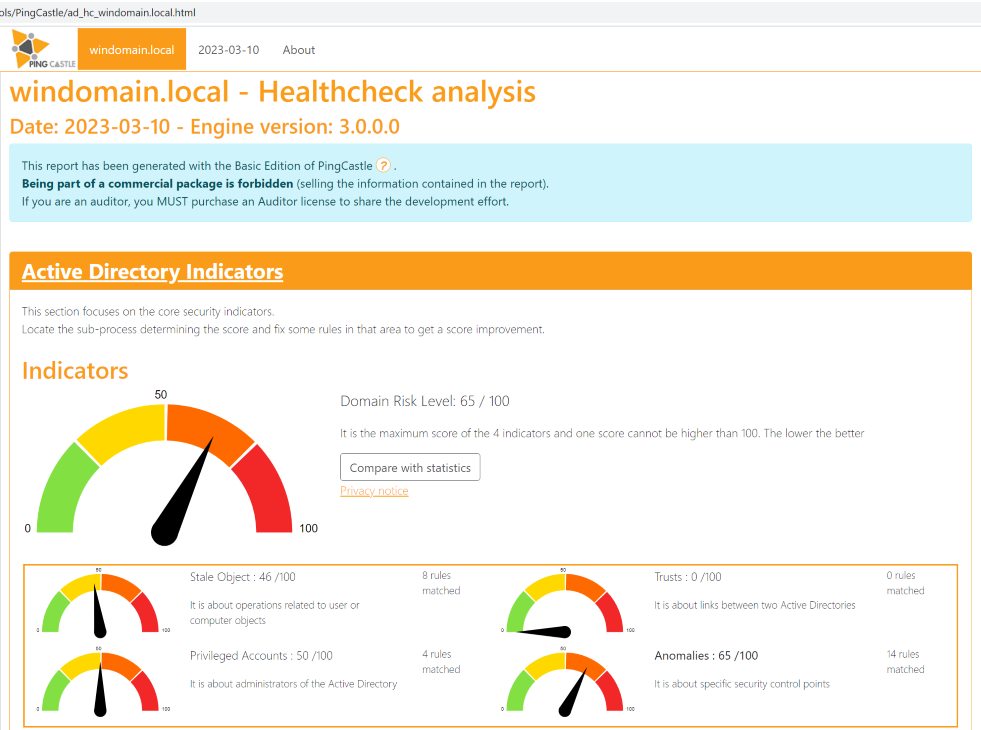
Below this is a tabular overview of the risks per indicator, the Risk Model. The color coding helps you with the prioritization. However, the risks should also be evaluated in the context of your own environment, which may result in changes in prioritization.
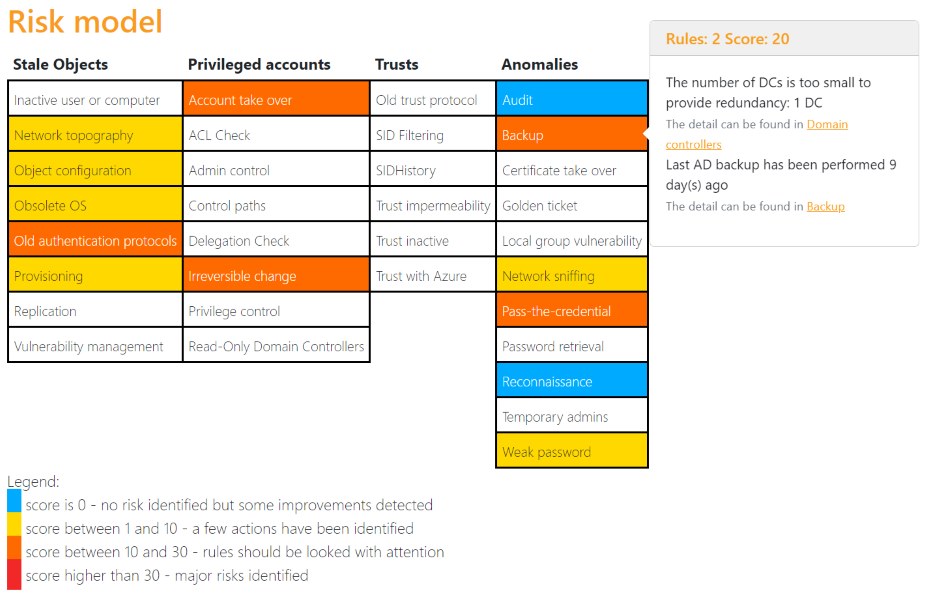
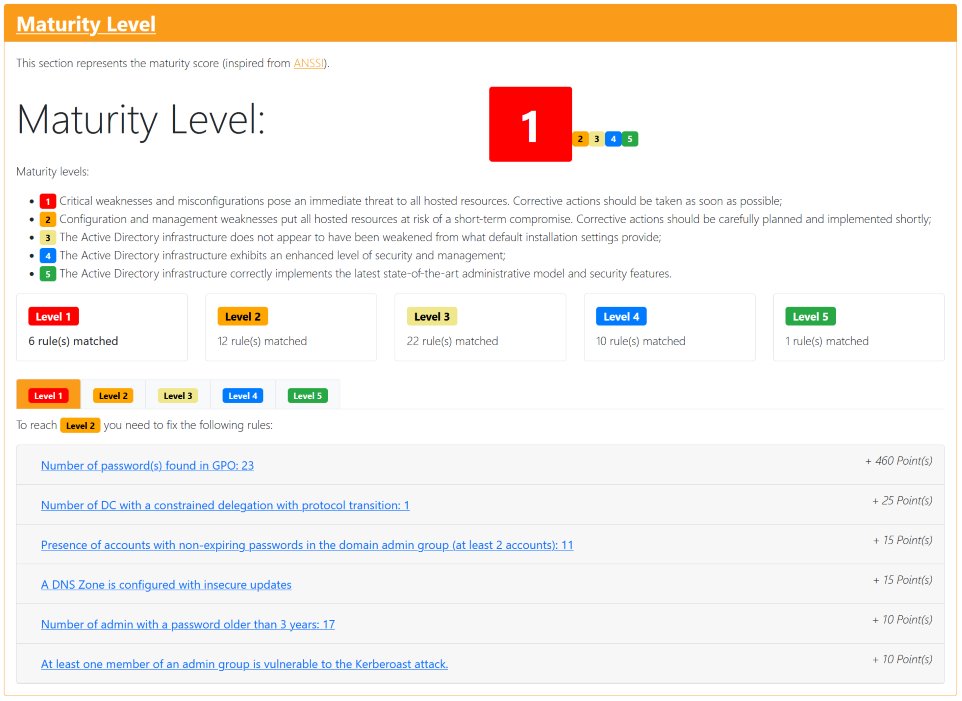
Clicking on individual entries in the table displays brief information about the risk, including a link to the raw data further down in the report. Below the Risk Model is the Maturity Level section, which lists the detected vulnerabilities. The vulnerabilities of the different maturity levels can be displayed by selecting the appropriate tab. Clicking on individual vulnerabilities in the list displays technical details of the vulnerability as well as recommended measures and links to further information.
Somewhat hidden in the control path analysis table, there are links that open analyses in the form of graphs. In these graphs, the relationships of various objects of the Active Directory are shown, and details about the relationships are displayed when hovering over the connection with the mouse.
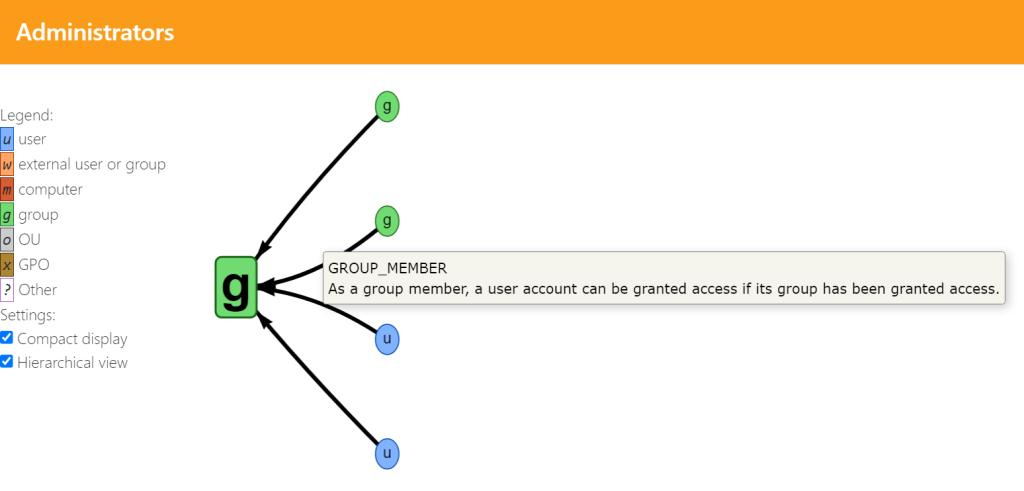
These graphs can be used to identify possible attack paths that may lead to, for example, privilege escalation in the AD environment. They are similar to the graphs that can be generated with BloodHound. BloodHound is often used to look for potential attack paths in AD environments. An example of such attack paths are paths to the domain administrator’s account or other privileged user accounts.
Password Check With “Have I Been Pwned?”
A crucial building block for Active Directory security is strong passwords. You should not just look at highly privileged accounts – any device connected to the Active Directory can serve as a gateway for attackers. Strong passwords protect against various attacks such as kerberoasting, password spraying, and brute-force attacks on intercepted password hashes (this is the form in which passwords are stored). Recommendations on password policies for strong passwords can be found in our blog article “Passwords: Common Mistakes, Best Practices & Tips”. To check password security in your own Active Directory, password hashes can be checked against known password hashes from data leaks.
The Australian security expert Troy Hunt operates the services “Have I Been Pwned” and “Pwned Passwords”. The latter is a collection of known compromised passwords or rather their hashes. This treasure trove of data can be downloaded for offline use. The PwnedPasswordsDownloader has meanwhile become available for this purpose – it requires .NET 6.0. The PwnedPasswordsDownload can be installed via PowerShell as follows:
PS > dotnet tool install --global haveibeenpwned-downloader
If the package is not found, adding the following package source will help:
PS > dotnet nuget add source https://api.nuget.org/v3/index.json -n nuget.org
The password hashes (SHA1, NTLM) can then be downloaded and saved as a text file using the following commands:
PS > haveibeenpwned-downloader.exe pwnedpasswords_sha1.txt
PS > haveibeenpwned-downloader.exe -n pwnedpasswords_ntlm.txt
The download takes a while because the download works via the HTTP requests to an API. By summer 2023, both files are between 30 and 40 GBytes in size.
Password Check With DSInternals
The cmdlet “Test-PasswordQuality” of the framework DSInternals allows to check the passwords in the own Active Directory for leaked passwords. The installation of DSInternals via PowerShell works as follows:
# Enable TLS1.2 on older versions of Windows
PS > [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
# Download the NuGet package manager binary.
PS > Install-PackageProvider -Name NuGet -Force
# Install DSInternals
PS > Install-Module -Name DSInternals -Force
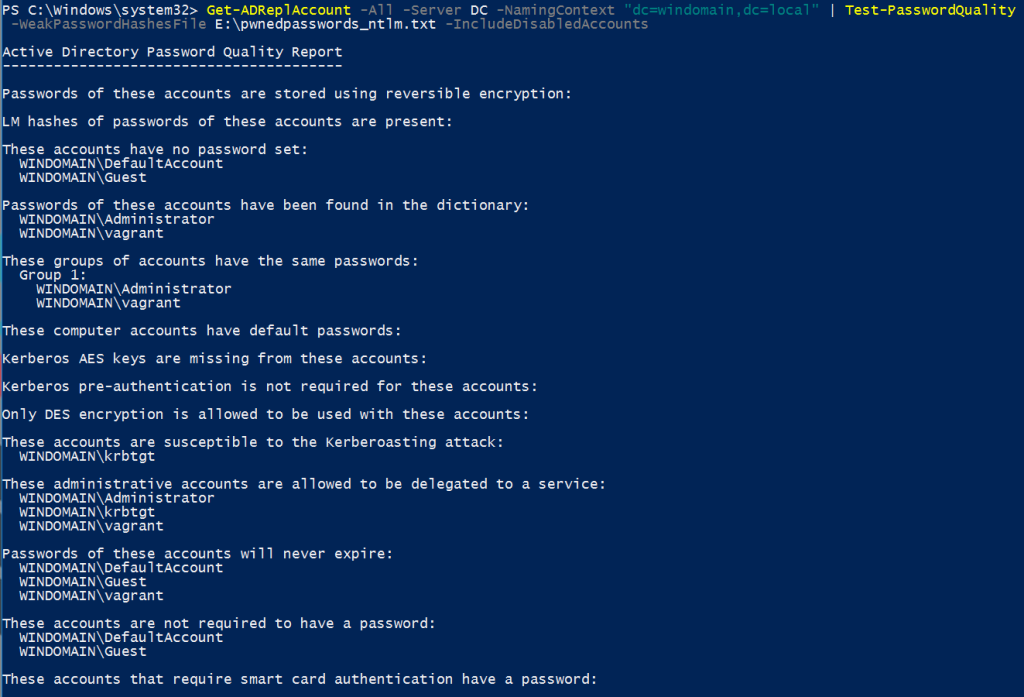
The “Test-PasswordQuality” cmdlet checks all AD passwords for weak entries, duplicates, default passwords or passwords that have not been set. The analysis can be performed online (DCSync) or offline (ntds.dit).
For the online option, the privileges of a domain administrator (or comparable) are required:
# Perform password quality test (DCSync)
PS > Get-ADReplAccount -All -Server DC -NamingContext "dc=windomain,dc=local" |
Test-PasswordQuality -WeakPasswordHashesFile E:\pwnedpasswords_ntlm.txt -
IncludeDisabledAccounts
For the offline option, a copy of the ntds.dit file must first be created, which contains the NT Hashes of the passwords. Since it is used continuously by the Active Directory, it is locked and cannot be copied in the conventional way. In the following, this is done via command line using a shadow copy:
C:\Windows\system32>vssadmin create shadow /for=C:
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Successfully created shadow copy for 'C:\'
Shadow Copy ID: {e776fc8c-8b9d-424e-a558-11db177a56f4}
Shadow Copy Volume Name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1I
C:\Windows\system32>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\ntds.dit C:\tmp\ntds.dit
1 file(s) copied.
C:\Windows\system32>reg SAVE HKLM\SYSTEM C:\tmp\SYS
The operation completed successfully.
C:\Windows\system32>vssadmin delete shadows /shadow={e776fc8c-8b9d-424e-a558-11db177a56f4}
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Do you really want to delete 1 shadow copies (Y/N): [N]? y
Successfully deleted 1 shadow copies.
This also created a copy of the registry entry “HKLM/SYSTEM”, since this contains the boot key for decrypting the copied ntds.dit. The password check with the PowerShell cmdlet “Test-PasswordQuality” then works as follows:
PS > $key = Get-BootKey -SystemHivePath C:\tmp\SYS
PS > Get-ADDBAccount -All -BootKey $key -DBPath C:\tmp\ntds.dit | Test-PasswordQuality -
WeakPasswordHashesFile E:\pwnedpasswords_ntlm.txt
If the error message “The database is not in a clean state.” is returned, ntds.dit must be repaired first:
# Repairing ntds.dit in case the error message “The database is not in a clean state.” is returnedPS > ESENTUTL /p C:\tmp\ntds.dit /!10240 /8 /o
Conclusion
The tools presented here are a good way of identifying basic misconfigurations in Active Directory yourself. iX’s “Hacking Yourself” series of tutorials presents even more ways to take a close look at your own IT environment (published so far: external network, web applications, internal network). Simple misconfigurations and weak passwords can thus be easily dealt with.
To identify more complex vulnerabilities and attack vectors, we recommend a detailed penetration test by our experts.
Awareness training by the Cyber Security Academy on the handling of passwords can serve as a contribution to sustainably secure passwords. We are happy to help you with these and all other cyber security topics. We look forward to hearing from you:





